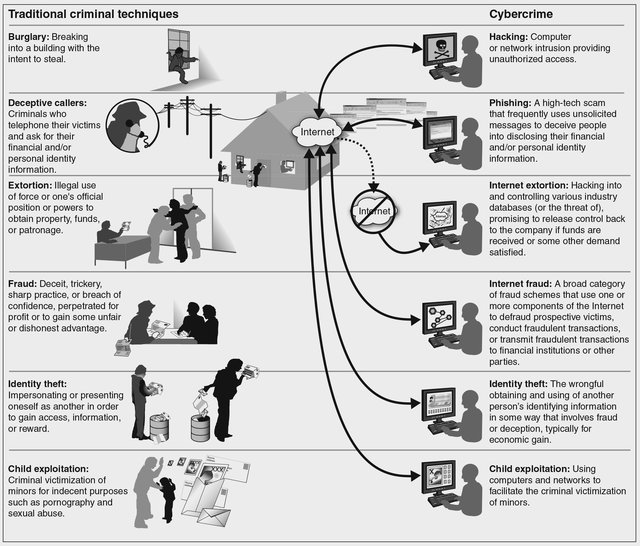
Computer Forensics involves obtaining and analysing digital. Identity theft and identity fraud are terms used to refer to all types of crime in which someone wrongfully obtains and uses another persons personal data in some way that involves fraud or deception typically for economic gain.
To counteract those computer-related crimes Computer Forensics plays a very important role.

. What Are The Most Common Ways That Identity Theft or Fraud Can Happen to You. The evidence lists directly help your security response team increase or reduce the importance of the security alert andor investigation of the related entities. Computer technology is the major integral part of everyday human life and it is growing rapidly as are computer crimes such as financial fraud unauthorized intrusion identity theft and intellectual theft.
Our adult based learning programs are interactive and are in use by numerous professional public safety entities. What Are Identity Theft and Identity Fraud. Defender for Identity security alert evidence lists provide the related entities that are involved in each potential lateral movement path.
OSS Academy provides quality online law enforcement corrections and telecommunications training courses. This includes critical peace officer jailer 911 telecommunications and security e-commerce training. LMP can now directly assists with your investigation process.
The National Sex Offender Public Website enables every citizen to search the latest information from all 50 states DC Puerto Rico Guam and Indian tribes for the identity and location of.

Identity Theft Investigations Pinow Com

Cyber Crime Investigation Making A Safer Internet Space

Tips And Advice To Prevent Identity Theft Happening To You Europol
Tackling Cyber Enabled Crime Will Require Public Private Leadership Centre For International Governance Innovation


0 comments
Post a Comment